Theory
Phases
- Agreement on Security Protocols
- 802.1X Authentication (if not WPA-PSK) + Association
- Key Distribution and Verification (Password-based if WPA-PSK)
- Data Exchange
WEP (Wired Equivalent Privacy) / TKIP and CCMP - encryption techniques
- WEP: Open or shared authentication; using RC4 ciphers + CRC32 checksum
- TKIP: Temporal Key Integrity Protocol
- CCMP: Counter Mode with Cypher Block Chaining Message Authentication Code Protocol (AES)
802.1X and EAP (Enterprise/Extensible Authentication Protocol)
- Resource: https://www.youtube.com/watch?v=bzWdE0Hc-jQ
- Network Authentication to Wireless Access Point to derive a Pairwise Master Key (PTK).
- EAP-TLS: Low level authentication protocol before TCP/IP since no IP address is assigned yet.
- 802.1X Port Control - controlled port only accepots EAPOL frames
- Supplicant EAPOL-Start –> Login Request –> Login Response to Authenticator Switch (e.g. Cisco Catalyst Switch)
- Authenticator –> Check Policy Database –> Informs Switch –> Switch enforce policy to Cisco ISE
- Derive the PMK - Pairwise Master Key
4-Way Handshake
- Resource: https://www.youtube.com/watch?v=9M8kVYFhMDw
- Using the PMK to derive a Pairwise Transient Key (PTK) - which is a data encryption key
- This occurs after open system authentication and 802.1X EAP association
- Access Point sends Anonce
- Client generates PTK and sends Snonce + MIC to validate by PTK by AP
- GTK (Group Temporal Key) is calculated by AP standalone, sends GTK + MIC to protect the frame
- Client OK
- Inputs to encryption key: PMK + Anonce + Snonce + AP MAC + Client MAC
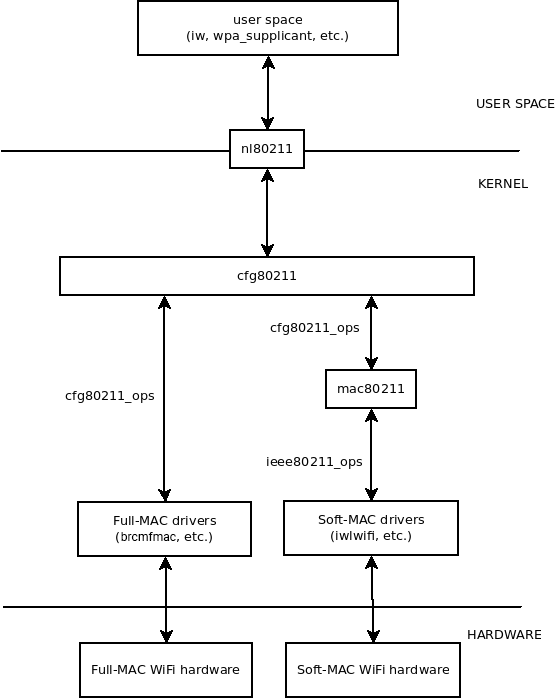
How mac80211 Wireless Framework interacts with each other