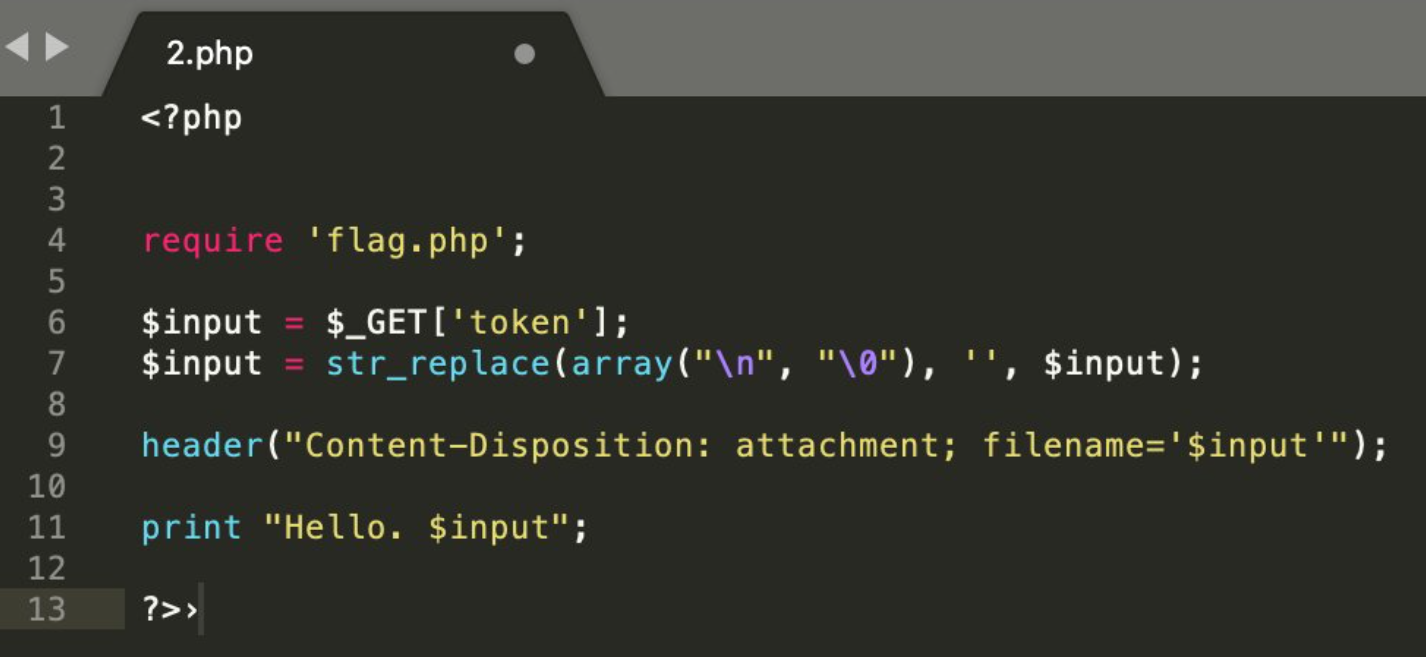
Type-Casting to String Bypass
- Bypass integer type using string
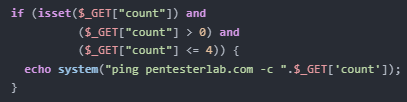
hash_hmac Array() Bypass
- Setting array() when expecting string type
hash_hmacvalue will result to NULL- Remove other parameter to also equal to NULL
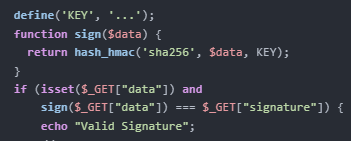
- Loose comparison between NULL and “” can also bypass
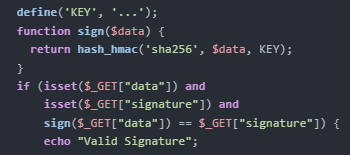
- Other Resources:
- https://ctftime.org/writeup/8573
- https://securify.nl/blog/spot-the-bug-challenge-2018-warm-up/
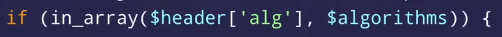
Insecure Regex
- Need to use
$to end the string - Array() can also cause failure to compare: https://bugs.php.net/bug.php?id=69274
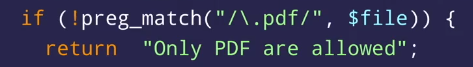
In_array() loose comparison
- in_array() without third variable is a loose comparison
Escaping HTML filters
PHP Type Juggling Vulnerability
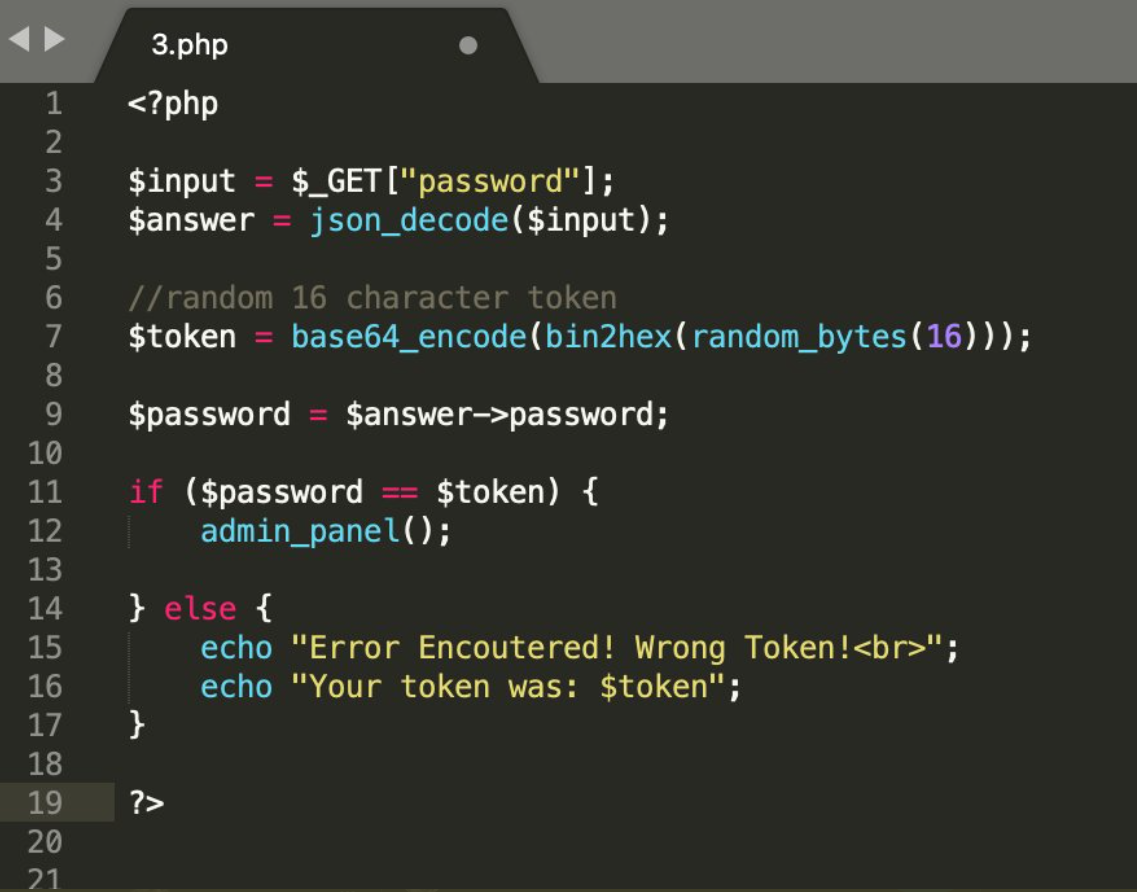
Using “==” is loose comparison in PHP, all we need is to set password={“password”:True} to successfully login.
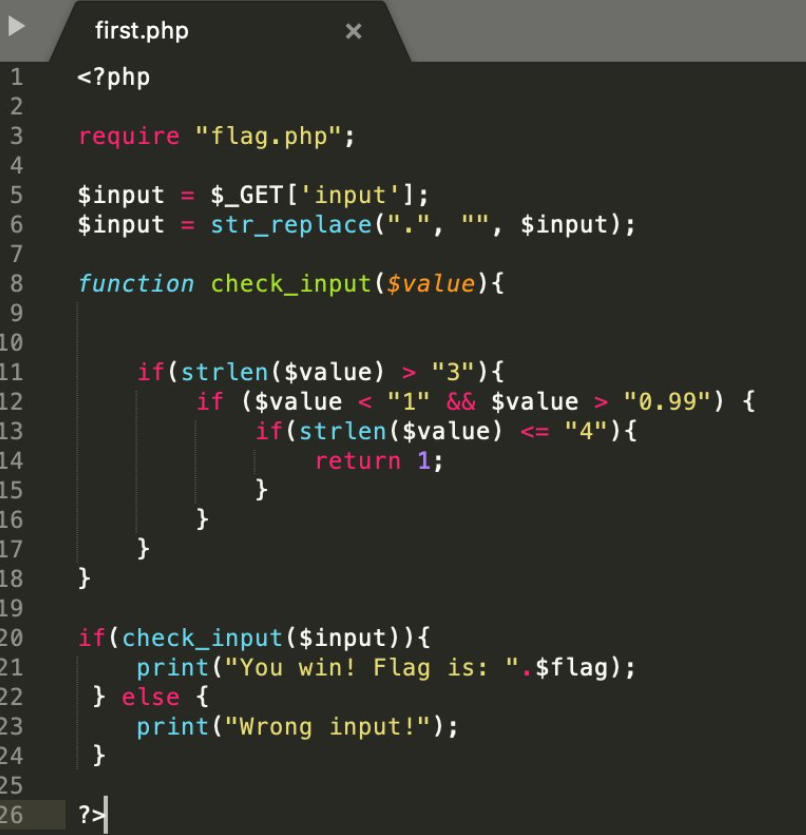
String comparison using 0xFF
HTTP Response Splitting in PHP