=======================================================
Basic Exploitation against Microservices (OSWE)
- Microservices are potentially vulnerable to SSRF issues.
- Identify microservice endpoints via enumeration (/file, /users, /render)
- Different in error status code and response length can reveal endpoints
- Identify routes for each microservice endpoint
- Using verb tampering (GET, POST, PUT, PATCH, DELETE)
- Use a wordlist to enumerate
- Server-side Request Forgery:
- If information can be returned: easy win
- Otherwise: potential blind SSRF (see below)
Blind SSRF
- Port scanning internal services using cURL or python scripts
- Scanning accessible subnets:
- First scan the gateway of internal ranges (192.168.X.X, 172.16.X.X, 10.X.X.X etc)
- Find services/microservices that can communicate with original server
- If other microservices are found:
- Could potentially relate to other endpoints found in earlier enumeration
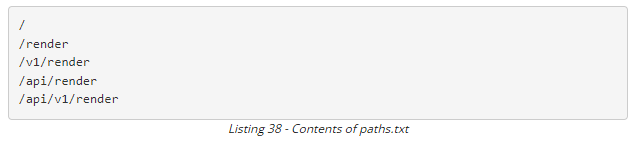
- Enumerate for valid endpoint using wordlist, as shown:
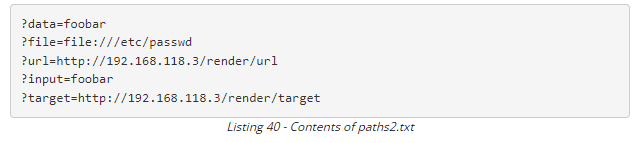
- Also enumerate for valid parameters, as shown:
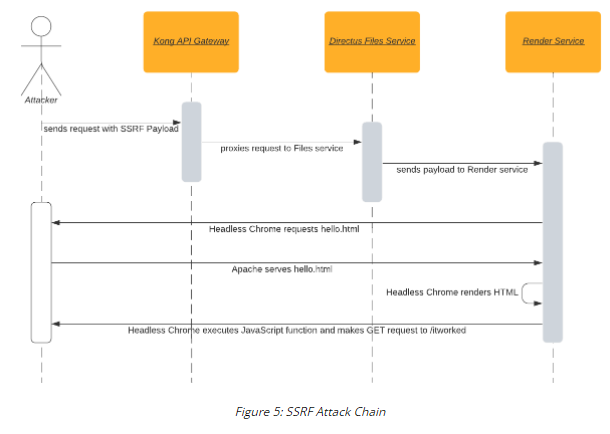
SSRF in Headless Chrome
- If SSRF found in Headless Chrome (verified by sending request to local machine)
- Verify that we can execute arbitrary Javascript (https://github.com/qwutony/notes/blob/main/Proof%20of%20Concepts/SSRF%20-%20itworks.html)
- This will increase blind to actual SSRF with real impact
- If microservice and uses user-defined bridge network in Docker (https://docs.docker.com/network/bridge/#:~:text=User%2Ddefined%20bridges%20provide%20automatic,other%20by%20name%20or%20alias.):
- Other ports on the same network are exposed internally
=============================================================
Cloud-based SSRF
https://book.hacktricks.xyz/pentesting-web/ssrf-server-side-request-forgery/cloud-ssrf
Post Authentication SSRF in JAMF
https://blog.assetnote.io/2021/11/30/jamf-ssrf/
Bypassing Deny Rule by using a trailing dot
- https://hackerone.com/reports/1410214
