Wi-Fi works over radio waves, which means it is subject to eavesdropping and therefore, encryption has to be used to protect the transmitted data.
https://security.stackexchange.com/questions/242502/why-do-wep-wpa-wpa2-need-tkip-aes-ccmp
Open Wireless Networks
- Public hotspots and older mesh networks
- STA authentication request to AP
- AP authenticate client
- Client associate with AP and join network
- AP associate client
WEP (Wired Equivalent Privacy)
- WEP aims at providing some degree of privacy to data exchanged on the wireless network.
- Secure wireless networks using Rivest Cipher 4 (RC4)1 to encrypt traffic and performs CRC32 checksums for message integrity
- RC4
- RC4 is a symmetric cipher, meaning that the same key is used to both encrypt and decrypt the data.
- It creates a stream of bits that are XOR’d with plain text to get the encrypted data. To decrypt it, we can simply XOR the encrypted text with the key stream in order to recover the plain text.
- Key Scheduling Algorithm (KSA): Initializes the state table with the IV and WEP key
- Pseudo-Random Generation Algorithm (PRGA): Creates the keystream
- WEP Authentication
- Open Authentication
- In open authentication, a client does not provide any credentials when authenticating to the Access Point. However, once associated, it must possess the correct key to encrypt and decrypt data frames.
- Shared Authentication
- During authentication, a challenge text is sent to the client. The challenge text must be encrypted with the WEP key by the client and sent back to the AP for verification.
- Open Authentication
- WEP can be cracked in under a minute
WPA (Wi-Fi Protected Access)
- Develop two new link layer encryption protocols: Temporal Key Integrity Protocol (TKIP, WPA1) and Counter Mode with CBC-MAC (CCMP, WPA2).
- WPA Personal: Makes use of pre-shared key authentication (WPA-PSK), a passphrase shared by all peers of the network.
- WPA2-PSK or WPA Personal does not use a central server for password veritifcation
- It’s generally accepted that a single password to access Wi-Fi is safe, but only as much as you trust those using it.
- WPA Enterprise: Uses 802.1X authentication and a Radius server for Authentication, Authorization, and Accounting (AAA).
- WPA Personal: Makes use of pre-shared key authentication (WPA-PSK), a passphrase shared by all peers of the network.
- Connection Process
- Agree on security protocols
- 802.1X authentication (or skipped if WPA-PSK)
- Keys distribution and verification + Master key distribution by Radius Server
- Data encryption and integrity
- Two ciphers are available, TKIP, for legacy hardware that can only handle WEP, and CCMP, that is based on Advanced Encryption Standard (AES).
- TKIP
- Backward compatible with legacy hardware
- CCMP
- It makes use of a new AES-based algorithm. It was designed from the ground up and is not compatible with older hardware.
- TKIP
- Steps:
- AP and STA will negotiate on authentication means (WPA-PSK or WPA 802.1X AAA) and the encryption suite (TKIP or CCMP)
- Then join network via open authentication + association
- The actual authentication process is based on the 802.1x policy and comes in several different systems labelled EAP. WPA Enterprise uses authentication via:
- EAP-TLS + client/server certificates
- EAP-TTLS
- PEAP for hybrid authentication
- https://www.securew2.com/solutions/wpa2-enterprise-and-802-1x-simplified
- Several EAP messages, depending on the authentication mode, will be exchanged between the authenticator and the supplicant in order to generate a Master Key (MK).
- At the end of the procedure, if successful, a “Radius Accept” message is sent to the AP containing the MK and another message, an EAP message sent to the client to indicate success.
- Network Authentication: 802.1X and EAP: https://www.youtube.com/watch?v=bzWdE0Hc-jQ
- 4-way handshake: https://www.wifi-professionals.com/2019/01/4-way-handshake
- https://www.youtube.com/watch?v=9M8kVYFhMDw
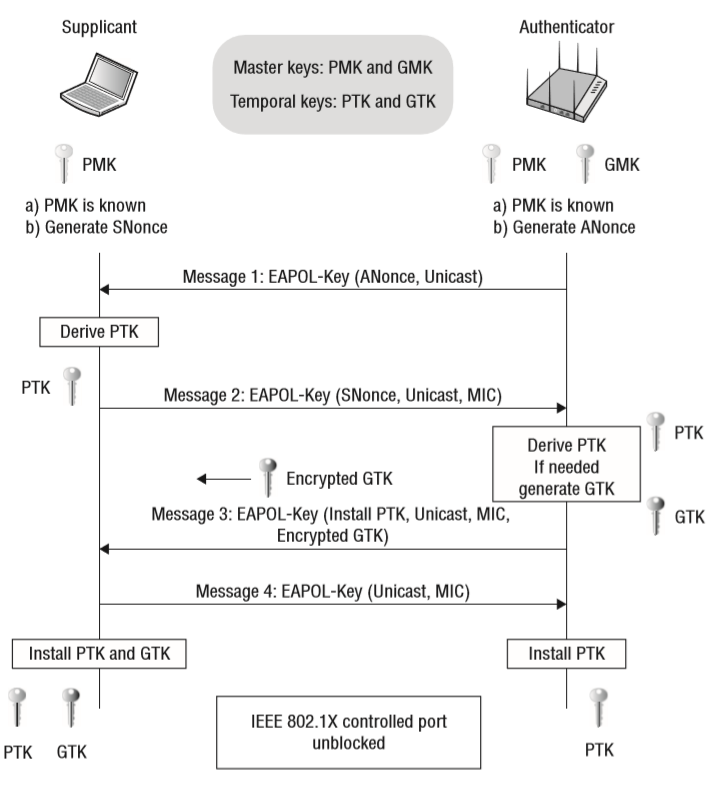
- In order to derive a PMK from that equation, one would have to break AES/RC4 (depending whether WPA2 or WPA is used). It is not that easy as the only practical approach is to perform a brute-force or dictionary attack (assuming you have a really good dictionary).
- https://www.youtube.com/watch?v=9M8kVYFhMDw
WPA3 (Wi-Fi Protected Access 3)
- WPA3-PSK (WPA3-SAE) - uses Simultaneous Authentication of Equals (SAE) to make brute-force dictionary attacks far more difficult for a hacker.
- A new 192-bit mode for enterprise networks with stronger cipher suites
- Mandatory use of Protected Management Frames (PMF), from 802.11w
WPS (Wi-Fi Protected Setup)
OWE
- Opportunistic Wireless Encryption (OWE), also known as “Enhanced Opened”, adds encryption to public Wi-Fi networks.
